Category Archives: Authentication
Delegation’s what you need (for usable security)
I heart PINs is a sorry tale of failed delegation (of a burglar alarm PIN). That failure was two-fold. Firstly, delegating a static shared secret such as a PIN or password invariably results in it being written down. Once written down the PIN has become a bearer token, fundamentally changing the security properties of the system. This introduces new threats whilst potentially mitigating others (given the importance of availability, loss of the token is a significant concern).
Continue reading Delegation’s what you need (for usable security)
Pico: No more passwords!
My work at the University of Cambridge:
If you want to know more, buy the Observer this weekend 26th-27th July (possibly maybe…probably not).
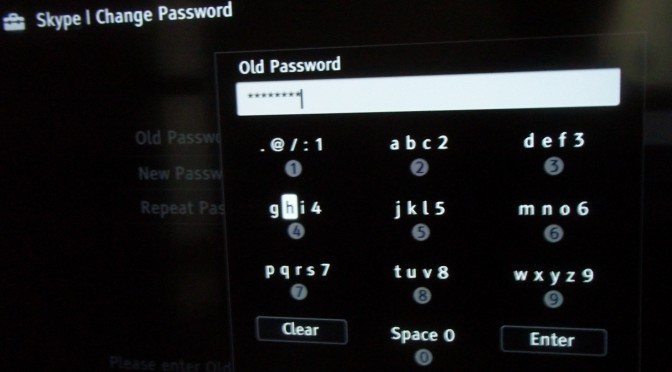
Smart TV dumb password
Making Skype calls using a Smart TVs is actual well…pretty smart. TVs have a nice display, good sound, and they’re usually located somewhere pretty where you can gather the whole family round for that cheery Christmas message of goodwill. Unfortunately Smart TVs bring the misery of web passwords straight to the comfort of your own living room…
Terrified by VISA
Whilst physical security measures are the sole responsible of the home owner, service providers on the Web frequently impose unworkable security mechanisms on their users. Here’s one cautionary tale of how this goes bad even for a security researcher.